- Apache Reverse Proxy Httpd Conf Example
- Apache Reverse Proxy Https To Http
- Apache Reverse Proxy Https
- Apache Ssl Reverse Proxy
Configuring an Apache-Server as Reverse-Proxy on Ubuntu
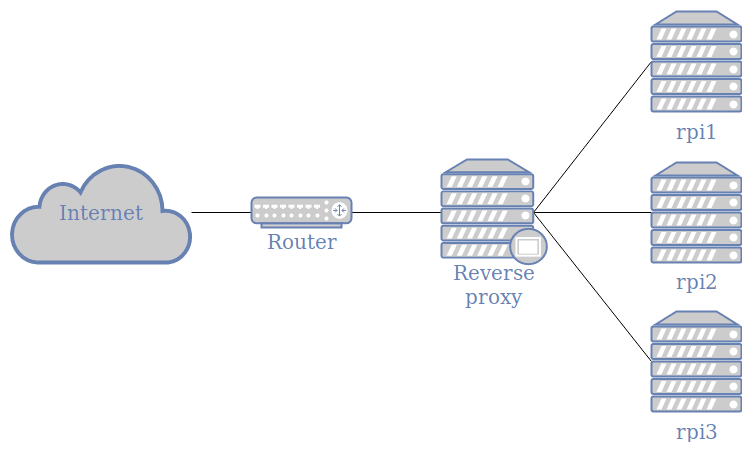
Reverse-Proxy – A useful Tool
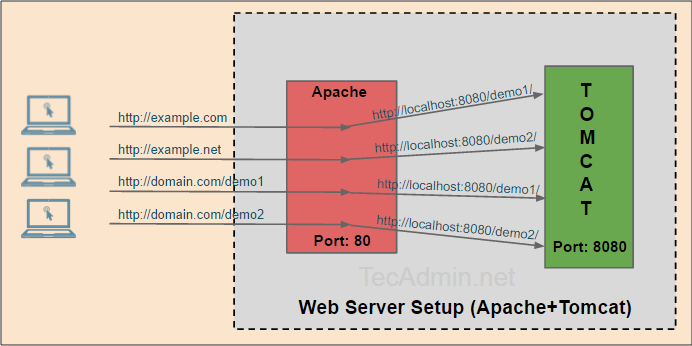
A reverse proxy is a tool that intercepts and handles http(s) requests. The reverse proxy can forward it to different servers, caching the response, thus relieving the underlying web servers or distributing the load to uniformly different systems. All in all, a very handy tool for busy services or multiple small servers.
Today I’ll show you how to build a proxy with Apache, which converts your requests from http to https, including a valid certificate, and then redirects them to two more servers. If the other two systems are in the same local network, you can forward the request via http. If your servers use public IPs, you should protect the forwarding with https. I’ll show you how to do both methods.
On the reverse proxy server, install apache web server and enabled the required modules by executing the lines below in terminal sudo apt-get install apache2 -y a2enmod proxy a2enmod proxyhttp a2enmod proxyajp a2enmod rewrite a2enmod deflate a2enmod headers a2enmod proxybalancer a2enmod proxyconnect a2enmod proxyhtml service apache2 restart.
Prepare the server and install Apache2
- –Check first the Apache HTTPS: use a directive DocumentRoot instead of the ProxyPass/ProxyPassReverse to test the connection (for example DocumentRoot “/var/www/html/test.html”).
- Reverse Proxy Guide. Available Languages: en. In addition to being a 'basic' web server, and providing static and dynamic content to end-users, Apache httpd (as well as most other web servers) can also act as a reverse proxy server, also-known-as a 'gateway' server. In such scenarios, httpd itself does not generate or host the data, but rather.
First you need a server with Ubuntu 16.04 LTS. Create one quickly on the Cloud provider of your choice and then continue here.
How to create a Server on gridscale, I will show you here:How to gridscale. Creating a Server on gridscale takes just a few seconds.
Before we turn your server on, you have do a bit of preparation first: Your domains A-Record must be set to the IPv4 address of your server and the AAAA record to the IPv6 address of your server. How this works, depends on your domain provider.
After both records are set, you can connect via SSH to your server. The, update your server with the following command:
Now install Apache and Let’s Encrypt. (If you want to build your Reverse-Proxy without a domain, you can skip the points on Let’s Encrypt):
Once the installation is complete, edit the config for your Virtual Host. For the sake of simplicity I use nano, of course you can use an editor of your choice:
Here you enter your domain in the first line so the result looks something like this:
Of course you have to replace the highlighted part with your domain. Next, specify the ServerName and ServerAlias below:
If you use a sub-domain, you can simply omit the serverAlias.
The entire config should look something like this:
Let’s Encrypt: Create a certificate for your domain
Then it’s time for Let’s Encrypt. Use the following command to create a new certificate for your domain and configure the redirect to https:
There are two options from here. The server behind the proxy can either be reached via a public or local IP. I recommend to make the servers accessible with Let’s Encrypt via https. Alternatively, you can also create an http connection.
First, I’ll show you the recommended variant for https connections.
Replace the part between <VirtualHost …> And </VirtualHost> With the following details:
In the End it should look like this:
If you do not want to use https between your servers, you need to edit the first file as follows:
In this file you can delete everything between the VirtualHost tags and replace them with the following text:
Either way, save the config and exit nano. Enable a couple of mods and reboot Apache and then we’re already to go.
Summary
With these simple steps, you can build your own reverse proxy, balancing the load on your servers. As well as the the examples shown here, a reserve proxy can be used for many other purposes, including Web Acceleration and Anonymity.
Reverse-Proxy – A useful Tool A reverse proxy is a tool that intercepts and handles http(s) requests. The reverse proxy can forward it to different servers, caching the response, thus relieving the underlying web servers or distributing the load to uniformly different systems. All in all, a very handy tool for busy services or multiple […]
Thank you for your feedback!
We will get back to you as soon as the article is finished.
Introduction
In this document we are using Apache 2.4.17 x64 from Apache Haus. Please note that CA does not officially endorse Apache Haus or this specific version of Apache httpd for windows over any other httpd distribution/version, it is just the one I am using for this document.
There will be three servers involved in this scenario:
1. <LBSERVER> is the load balancing server. This is the server where we are installing Apache httpd.
2. <ENTM> is the primary Enterprise Management server
3. <LBENTM> is the load balancing Enterprise Management server
The assumption has been made that both <ENTM> and <LBENTM> are installed and working and serving SSL from port 18443. It is very important that this is the case. There is no point in implementing a reverse proxy to servers that do not work themselves, it just adds an additional layer to debug.

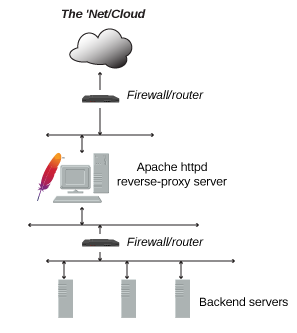
The aim is to have Apache httpd serving SSL on only port 8443 on <LBSERVER> acting as a reverse proxy to <ENTM> and <LBENTM>. No other ports will be served by Apache httpd.
Apache Reverse Proxy Httpd Conf Example
I have also added a rewrite to that users who go to https://<LBSERVER>:8443/ will automatically be redirected to https://<LBSERVER>:8443/iam/ac.
***** YOU MUST MAKE SURE THAT NOTHING IS RUNNING ON PORT 8443 on <LBSERVER> BEFORE CONTINUING *****
Use the following command to determine if anything is running on port 8443:
If it returns nothing then nothing is running on port 8443 and you are set to go.
Section 1 - Download and Install Apache 2.4.17 x64:
1. On <LBSERVER> go to the following url:
Download:
A) Apache 2.4.x VC11 -> Apache 2.4.17 x64
B) Microsoft Visual C++ 2012 Redistributable
I will refer to the folder you have downloaded these files to as <download> from here on.
2. Unzip httpd-2.4.17-x64-vc11.zip to <download>httpd-2.4.17-x64-vc11.
3. Open <download>httpd-2.4.17-x64-vc11readme_first.html and review the installation instructions. I have included installation instructions below, but they may need to be adapted for your system or due to and changes made by Apache Haus if you are using a different version of Apache httpd 2.4.
4. Copy the <download>httpd-2.4.17-x64-vc11Apache24 folder to c:, so you have a c:Apache24 folder.
Section 2 - Generate the SSL keys and certificate
1. On <LBSERVER> open a command prompt and navigate to c:Apache24bin:
2. On the command prompt, run the following command:
Follow the prompts as requested (***** remember any pass phrases etc that you use! *****) When finished this will have created two files:
3. On the command prompt, run the following command:
Follow the prompts as requested. This will create the following file:
4. On the command prompt, run the following command:
This will create the following file:
5. The following files should now exist:
Section 3 - Configure Apache httpd
1. on <LBSERVER> edit C:Apache24confhttpd.conf.
To comment out a line in httpd.conf place a # symbol at the beginning of the line.
To uncomment a line in httpd.conf remove the # symbol at the beginning of the line.
Comment out:
Find the following lines and uncomment them. These lines are not contigious so will need to be found and uncommented one by one:
Apache Reverse Proxy Https To Http
Find:
And change it to something appropriate e.g. replacing <LBSERVER> with the FQDN of your this server:
Add at the end of the file add the following lines, replacing <ENTM> and <LBENTM> with the hostname or FQDNs of the ENTM and load balancing ENTM respectively, and <LBSERVER> with the FQDN of this server:
2. Edit extrahttpd-ahssl.conf:
Comment out:
Comment out all of the following lines:
Section 4 - Starting And Testing Apache httpd, And Making It A Service
It is possible and easy to setup Apache httpd to run as a windows service, but we will test it first by running in a command prompt to see if there are any errors. Note that debugging errors for Apache httpd is beyond the scope of this document - any errors I came across I fixed in the configuration above - and CA Technical Support. However, Google is your friend. Apache httpd is the most widely used web server on the internet so if you encounter a problem, someone probably already has and has a solution, at least that was my experience when writing this document.
1. On <LBSERVER> open a command prompt and navigate to c:Apache24bin:
2. Start httpd:
After entering the command wait a few seconds. httpd should stay running and not return to a command prompt. If it does and/or any errors are displayed they will need to be investigated and resolved before continuing. To stop it just press CTRL + c in the command prompt. After a second or two it will stop.
3. Make sure httpd is running as per step 2, and log in and test by pointing a browser to (where <LBSERVER> is the hostname or FDQN of the server we have installed Apache httpd to):
You may be prompted with some SSL warnings due to using a self signed certificate as per Section 2 - Generate the SSL keys and certificate. Once past these you should be presented with the ControlMinder/PIM login. Test a few things.
4. Assuming everything appears to be working, run a few different browser sessions (that is different session, not just different tabs or windows of the same browser session) on different client machines.
Open c:Apache24logsproxy-access.log and you should see entries like the below:
123.123.123.123 is the IP Address of the client where the browser is running.

https://<ENTM>:18443 will be either the hostname/FQDN of the ENTM or LBENTM. There should be a good mix of <ENTM> and <LBENTM> to show that the load balancing is working - if you have used different browser sessions, opening new tabs and/or windows of existing browser sessions does not work to test this.
https://<LBSERVER>:8443 is the hostname/FQDN of the server we installed Apache httpd on.
Apache Reverse Proxy Https
5. Once you are satisfied that Apache httpd is running as a reverse proxy correctly, we can set it up as a service. Open a command prompt and navigate to c:Apache24bin
6. Execute the following command:
This will return something like:
There should be no errors as we have already fixed them before progressing from step 2.
7. In Windows Services, there should now be an Apache2.4 service. This is stopped and started like any other service. By default this is set to start automatically when the server is started, you may or may not want to change this.
Apache Ssl Reverse Proxy
You have now finished installing the reverse proxy/load balancer.
